Statistical data shows that over one-third, or 36 percent, of ransomware infections happen due to a lack of cybersecurity training across organizations across all industry verticals. Another 30 percent of the ransomware infections worldwide materialize because of weak user passwords, while 25 percent are due to poor user practices, according to managed service providers (MSPs) surveyed.
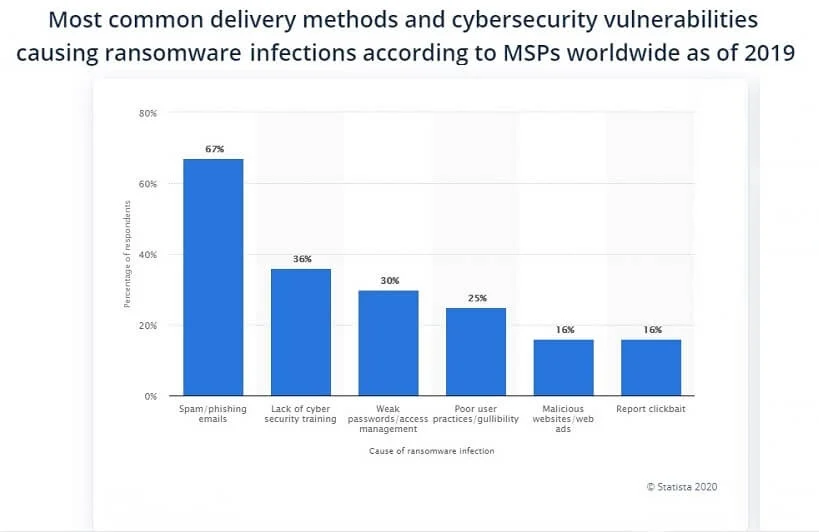
Source: Statista
It all starts with educating organizations from the bottom up on cybersecurity, beginning with the basics.
A simplified definition of cyber resilience is a method and framework measuring how well an organization can cope with cyberattacks or data breaches while retaining business continuity. Cyber resilience is a preventive measure that ensures the organization's core processes are still operational should a cyber-attack penetrates the perimeter defenses and how to prevent this from happening in the first place.
Organizations need to educate and train their employees to minimize human error and bad user practices to an acceptable minimum since these are the two weakest points in any cyber-defense strategy.
It all starts with the basics: if users are unaware of cyber-threats and how they work, they cannot spot one or avoid poor security practices. Furthermore, uneducated and untrained employees won't respond appropriately once they detect malware in action or when they see suspicious account or application behavior.
The cost of letting uneducated and inexperienced users accessing business-critical systems and networks, especially in increasingly remote workforce environments, is always high. Human error and harmful practices such as weak passwords and connecting from insecure Wi-Fi networks are the scenarios every hacker in the world are trying to exploit to their best benefit.
A single ransomware infection due to a weak user password or a user using a public Wi-Fi hot spot for work can ruin an average enterprise's business and paralyze its operations for weeks.
Therefore, organizations must make every effort to educate their employees on the basics of cybersecurity. Training should include how to spot phishing emails, detect unusual app and account behavior, and to respond to any actual or possible cyber threat they happen to see.
Building a cybersecurity culture and training employees in IT best practices should not be an expensive or daunting task for the average enterprise. It is a cultural transformation problem, not necessarily investing heavily in security tools or lengthy and unpopular training programs.
In the end, having a working and practical culture of cybersecurity is all about creating a security-conscious mindset that prevents cybersecurity incidents from occurring by minimizing human errors and bad user practices.
The researchers at the Massachusetts Institute of Technology (MIT) have developed a framework reflecting the best practices of organizations that have managed to build excellent cybersecurity culture through educating and training their leadership and users in a security-aware way of working.
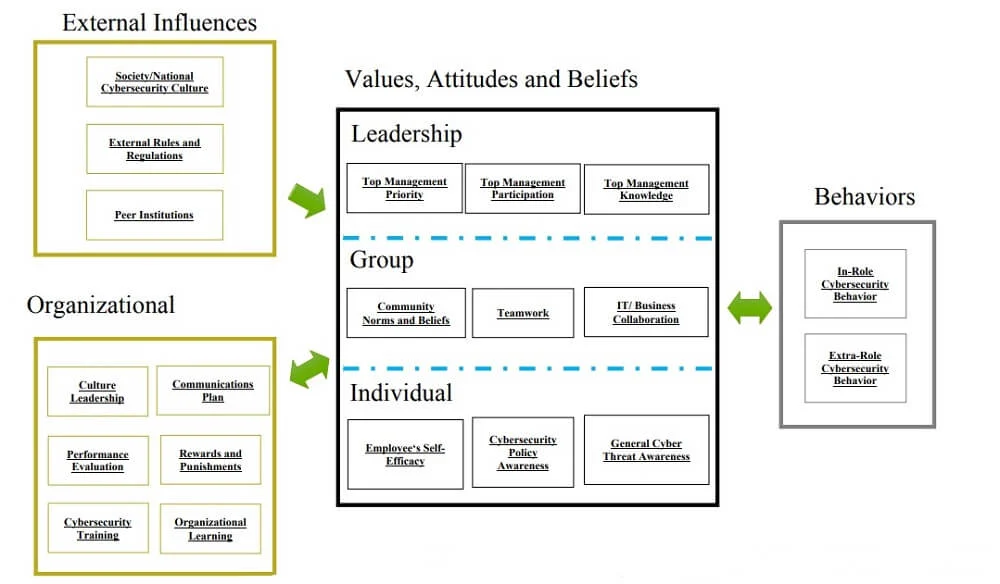
The framework above pertains to the overall approach toward a more secure corporate IT environment, showing the basic components of a transformational mindset that result in better cybersecurity for all stakeholders.
While each organization should draft a cybersecurity training strategy that best fits its particular needs, there are certain IT security areas, which every educational program should address.
Stolen, shared, and hacked passwords or other user access credentials are by far the most common way for bad actors to get access to sensitive corporate data or networks. The problem is that even if organizations force their users to enter strong passwords, the users still have dozens of other online accounts, which can cause problems if only one of them is compromised.
Passwords and login/sharing credentials are the first lines of defense, and as such, any training program should start with the basics of password protection.
Phishing emails are another critical attack vector with a high percentage of successful cyber-attacks relying strictly on email penetration to access essential business systems. Training employees to recognize phishing attempts on all communication channels is crucial for building a strong cybersecurity culture.
An organization cannot tell employees what applications to install at home, but users should be aware that installing and running unauthorized software on corporate machines is a bad practice. Furthermore, employees must train to respond immediately to any malicious app behavior and contact the IT support and security team.
Removable media are another source of possible troubles when IT security is concerned. At least two confirmed successful cyber-attacks on heavily guarded facilities such as nuclear power plants occurred using infected removable media.
Organizations should also educate their employees about the hazards of connecting their mobile devices to corporate computers as virtually any personal mobile device has multiple apps installed, and each of them is a potential security risk.
Educating employees about the cybersecurity risks should not leave the problem with physical security aside. While most business-critical data is stored in digital format, organizations still use paperwork in their daily operations, and employees should be trained to follow a clean-desk policy in the office.
Likewise, a lost or stolen device can cause a lot of trouble if there is sensitive information inside or if credentials enable a third party to login to corporate digital resources.
An organization can successfully run a Bring-Your-Own-Device (BYOD) policy, but there is still a need to educate the users not to connect their devices before scanned for malware and report any stolen or lost device.
Building a culture of updating and patching employees' mobile devices is another best cybersecurity practice.
The list of training and educational programs an organization can run to enhance its employees' overall cybersecurity awareness does not end there. Any organization has its specific areas to address and improve, as cybersecurity is a very far-reaching one while cyber threats and penetration methods evolve rapidly.
Industry reports such as the Annual Cost of Cybercrime Study by Accenture and Ponemon Institute show that malicious insiders are involved in cyberattacks resulting in organizations incurring losses averaging $1.6 million in 2018.
What is worse than a malicious insider though is a team of employees who are not aware of cybersecurity basics and where each team member is both a risk and a potential source of malware infection or compromised credentials.
With all types of cyberattacks on the rise, and with people-based attacks reporting the highest rate of growth, employee training and adoption of IT security educational programs should move to the top of the list for any organization aiming to secure their IT environment.
As cyber-threats are evolving and bad actors change their methods by the changing cyber-defense practices, organizations should adopt a flexible training approach with training programs running while being continuously updated to include new cyber threats and familiarize employees with the latest best cybersecurity practices.
Ready to take your cybersecurity strategy to the next level?
Contact us today for a no-cost consultation.
