Open source software is a rapidly growing market because every user has access to the respective programming code, can audit what the code’s functionality does and can edit the code to fit specific requirements.
Published
The overall market for open source is projected to stand at $21.6 billion in 2020 and then grow by over 30 percent by 2020, reaching close to $33 billion a year.
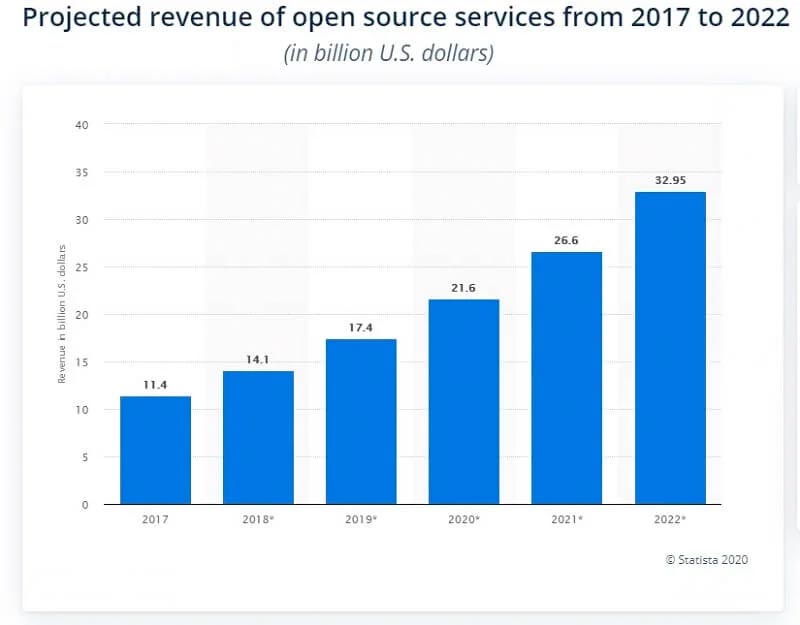
Source: Statista
Cybersecurity tools corner a large market share of open source software. There are plenty of free open source cybersecurity tools that meet requirements for enterprise-grade security software.
Unfortunately, many of the free open source security tools do not provide all the capabilities of the respective paid version. Many newcomers to cybersecurity use the free versions to learn and test before they purchase the full versions.
Many of the tools perform as expected and give your security team or a third-party software developer the ability to modify the programming code to meet your specific needs and requirements.
Small to Mid-size enterprises will often use a combination of free and paid open source tools to improve their organization’s cyber security and modify the solution to protect their digital assets and networks according to their unique business operation needs.
The open source cybersecurity software tools in this review are listed alphabetically:
Kali Linux is an open source Debian-based Linux distribution offering a variety of free software, cyber security utilities and penetration testing tools.
It is one of the few hacking-focused Linux distributions that comes pre-packaged with tools for reconnaissance and delivering payloads, as well as several other penetration-testing utilities.
Kali uses WSL (Windows Subsystem for Linux), which allows users to run Linux executable files directly from a Windows 10 system.
The Kali OS supports embedded devices such as Raspberry Pi, Beaglebone, Odroid, HP & Samsung Chromebook as well as well as Android OS.
KeePass is a free and open source password manager that securely stores passwords. This security tools enables users to have a single place for their unique passwords for websites, email accounts, webservers or network login credentials.
KeePass works by storing passwords in a secure database, which unlock by entering a single master key. Database encryption is using the most secure encryption algorithms available: AES-256, ChaCha20 and Twofish. It encrypts the complete database, which means user names, notes, etc. are being encrypted along with the password fields.
Metasploit Framework is an exploitation and vulnerability validation tool that you can use offensively to test your systems for known and open vulnerabilities.
This open source security tool is helping you to divide the penetration testing workflow into manageable sections, while you can also set up your own workflows.
It is also a tool for auditing and network port scanning, which scans approximately 250 ports that are usually exposed to external services. An auto-exploitation feature works by cross-referencing open services, vulnerability references and fingerprints to find corresponding exploits.
Nikto is a free and open source web server scanner, which scans web servers for multiple vulnerabilities. The testing covers more than 6,700 potentially harmful files/programs and makes checks for outdated versions of over 1,250 servers. The web server scanner finds version-specific problems on over 270 servers.
Users can also perform checks for server configuration issues such as the presence of multiple index files, HTTP server options. This open source security tool identifies installed web servers and software as well.
Nmap, Network Mapper, is used for penetration testing and security auditing. It uses NSE scripts to detect vulnerabilities, misconfigurations and security issues concerning network services.
Nmap maps network and ports before a security audit starts and then uses the scripts to detect any recognizable security problems. The app is fetching raw data and then determines a host type, type of operating system (OS) and all the hosts available within the network.
Network administrators can use Nmap also for performing tasks around network inventory, service upgrade schedules and monitoring uptime.
The open source security tool runs on Linux, Windows and Mac OS X. It is designed specifically for scanning large networks, but can be used to scan single hosts.
OpenVAS is an open source and full-fledged vulnerability scanner, free for use. Users can perform unauthenticated testing and authenticated testing for various high level and low level Internet and industrial protocols.
This tool also enables performance tweaking for large-scale scans. Users can perform any type of vulnerability test by taking advantage of its internal programming language.
OSSEC is an open source, scalable and multi-platform Host-based Intrusion Detection System (HIDS), whose creators want to keep free for the foreseeable future.
Use OSSEC on premise and in the cloud for the purpose of server protection or as a log analysis tool that monitors and analyzes firewalls, IDSs, web servers and authentication logs.
OSSEC can withstand cyber-attacks and system changes in real-time utilizing firewall policies, integration with third parties such as CDNs and support portals. The application features self-healing capabilities and provides application and system-level auditing for compliance with many common standards such as PCI-DSS and CIS.
Security Onion is a Debian-based Linux distribution for detecting threats, enterprise security monitoring and log management. It incorporates security tools such as Elasticsearch, Logstash, Kibana, Snort, Suricata, Zeek, OSSEC, Wazuh, Sguil, Squert, NetworkMiner and others to protect an organization against cyber threats.
It is an all-in-one open source security solution that provides users with various tools to detect threats and monitor their systems.
VeraCrypt is a security tool for disk encryption. It runs on Windows, Mac OSX and Linux and creates a virtual encrypted disk within a file before mounting it as a real disk.
This tool encrypts an entire partition (file storage drive) or storage device such as a USB flash drive or hard drive before dumping it the cloud or elsewhere. Users can also pre-boot authentication by encrypting a partition or drive where the Windows OS is installed.
VeraCrypt encrypts in real-time and supports hidden drives and hidden operating system on a machine.
Wireshark is a free and open source tool for network protocol analysis. This cybersecurity tool enables security professional to observe network at a microscopic level by viewing the traffic, dumping of specific packets, checking the packet format and finding network issues this way.
It is available for multiple platforms including Runs on Windows, Linux, macOS, Solaris, FreeBSD and NetBSD allowing for deep inspection of hundreds of protocols. Wireshark supports live capture and offline analysis of data and offers decryption for multiple protocols such as for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP and WPA/WPA2.
